Recent Posts of Security

03 July, 2025
Blockchain technology is revolutionizing the fintech industry with its ability to secure transactions, reduce costs, and improve transparency. From cross-border payments to smart contracts and fraud prevention, this blog post explores how blockchain empowers financial institutions and fintech startups to streamline operations and build customer trust.

30 May, 2025
It’s been another packed week in the software development universe! AI continues to drive innovation at a breakneck pace, core development tools are receiving significant upgrades, and as always, staying on top of security remains paramount. Let’s dive into some of the biggest headlines that caught our eye and what they mean for developers.

23 May, 2025
From GitHub Copilot’s upgrade with Claude 4 models to game-changing AI announcements at Google I/O and Microsoft Build, plus urgent Node.js security fixes — this week’s Developer Nation roundup gives you the essential insights you need to stay current in the fast-moving world of tech.
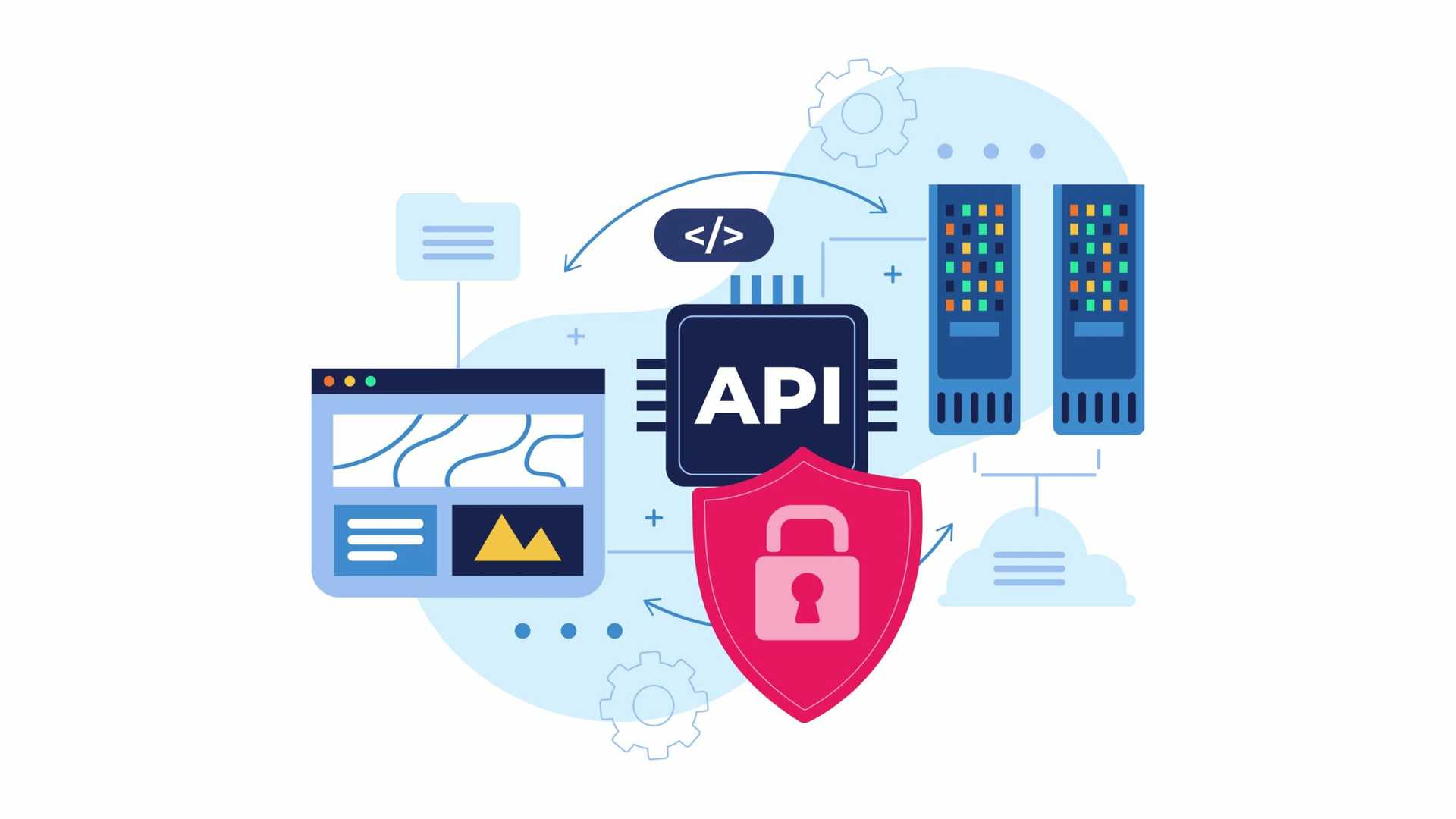
11 July, 2024
With the cost of cybercrime expected to reach $13.82 trillion by 2028, the issue of cybersecurity is very real. If you are developing REST APIs, what threats might you face, and how should you be tackling them? Should you have a checklist of best practices during development to minimize any potential threats?

25 June, 2024
In a data-rich world, businesses seek alternatives for information storage and sharing, creating opportunities for cloud developers. However, with these opportunities come risks, making it crucial to build a security-first culture through collaboration, robust protocols, and continuous training.

19 May, 2023
The average cost of a security breach in a hybrid cloud environment is estimated at a staggering $3.6 million making it critical for organisations to make software security one of the most important priorities.
Cisco’s most recent report, based on the findings from two SlashData global surveys that targeted enterprise developers, uncovers developers’ exposure to API security exploits, their outlook on security, and how they use automation tools to detect and remediate threats.

04 April, 2023
Rapid uptake in adoption by industries ranging from banking to retail to autonomous vehicles of customer- and partner-facing and internal application programming interfaces (APIs) to drive internet traffic has resulted in an equally rapid growth in endpoint attacks – more than 11 billion over just 18 months according to a report from edge computing security leader Akamai. It makes sense that they are more vulnerable to threats from malicious actors, given API endpoints’ similarity to internet-facing web servers, and their role as pipelines between divergent platforms.

12 March, 2014
App development is becoming more and more popular, as web and software developers are migrating to the mobile industry. Secure development on mobile applications, however, has not shown the same level of growth or maturity. This article sums the best ways to build secure apps. It concentrates on OWASP top 10 (and similar) vulnerabilities, as these are most commonly found in mobile apps.
08 February, 2013
The security features of an app are often ignored in the rush to get a new product to market. We naturally tend to focus more on what an app should do, rather than what it shouldn’t. Making sure that an app doesn’t have security flaws is a difficult and potentially expensive process. There are…
Contact us
Swan Buildings (1st floor)20 Swan StreetManchester, M4 5JW+441612400603community@developernation.net